My password manager setup (KeePassX + KeePassDroid + YubiKey + SpiderOak)
A while back, a couple of friends on Twitter were looking for password manager recommendations. The shared requirement was that it’s self-hosted, includes browser support and synchronizes with Android.
Some people suggested LastPass and other products, but my suggestion was as follows:
@iElectric KeePassX / KeePassDroid + host in title bar Chrome / Firefox extension + SpiderOak / Gdrive / Dropbox for sync
— Tomaz Muraus (@KamiSLO) October 15, 2013
I thought it would good to elaborate on it and describes pluses and minuses of this setup.
Password Managers
There are many programs for securely storing your passwords out there. The most popular ones include 1Password, LastPass, KeePass and Password Safe. 1Password and KeePass are native applications and LastPass is a service with plugins / extensions for popular web browsers.
LastPass being a service means that synchronization is transparently taken care for you. 1Password offers supports for synchronizing database file using Dropbox and in KeePass case, you need to manually take care of the database file synchronization.
I tested and played with all those applications in the past, but for almost 5 years now, I have been using KeePass(X). More details on my setup can be found in the section bellow.
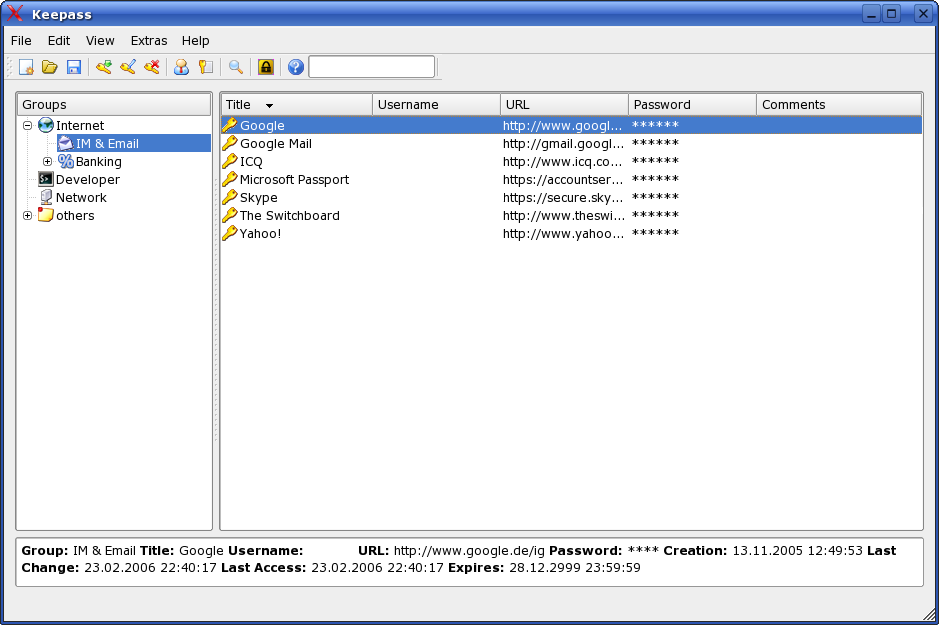 Main window of the KeePassX password manager.
Main window of the KeePassX password manager.
I believe that any component or application (including password manager) which deals with security or crypto should be open source. As such, my main problem with 1Password and LastPass is that those programs are not open source.
On top of that, LastPass is a service which means your data is stored on 3rd party servers by default and the main interface for accessing data is a browser extension which has all kinds of security implications.
LastPass website claims that all of the encryption and decryption is handled locally and passwords are never sent to their servers in plain text. Chrome extension does include native (npapi) component which is supposed to safely handle crypto, but I still trust native open source application way more than I trust closed-source binary browser plugins.
1Password does have relatively good documentation which describes which cryptographic algorithms are used and how, but this doesn’t make a difference and change the fact that the application is not open source.
Other big 1Password disadvantage (at least for me) is, that it doesn’t work on Linux.
My Password Manager Setup
I run Linux and only use Android devices, but all of the applications listed bellow should also work on Windows and OS X.
- KeePassX - Main password manager. It uses KeePass compatible database format which means that databases can also be opened by other applications which support reading database files in this format.
- KeePass Droid - Open source Android application which supports reading and writing KeePass database files. I use it on my Android powered phone and tablet.
- Host in title - Firefox and Chrome extension which adds hostname of the currently active website to the browser title bar. This is useful for finding matching entries in the KeePass database and automatically populating form fields on the websites using the “auto-type” feature in KeePass.
- YubiKey - This component is optional. I use YubiKey in a static password mode in combination with my regular must password to form a dual factor authentication. The first factor (something you know) is regular master password and the other factor (something you own) is static password provided by YubiKey.
- SpiderOak - I use it for synchronizing database files across multiple devices.
As noted above, this setup (minus the Android client) has been working perfectly for me for almost 5 years now.
 YubiKey
standard. If you want to use it with your Android device you will need
micro USB to USB adapter and need a newer version of Android which supports
USB
host mode. If this is too much for you but you still want multi factor
authentication, you can simply get YubiKey
NEO which can talk to your phone using NFC.
YubiKey
standard. If you want to use it with your Android device you will need
micro USB to USB adapter and need a newer version of Android which supports
USB
host mode. If this is too much for you but you still want multi factor
authentication, you can simply get YubiKey
NEO which can talk to your phone using NFC.
Compared to other programs mentioned above, main advantages of this setup are:
- All the components except SpiderOak client which is optional are open source.
- All the components are cross-platform. KeePass and KeePassX work on Windows, Linux and OS X. KeePass is a .NET application which works on Linux using Mono and KeePassX is a QT application.
Using SpiderOak or a similar service is optional. You only need to use it if you want to automatically synchronize database file across multiple devices. Other popular file synchronization services include Dropbox and Google Drive.
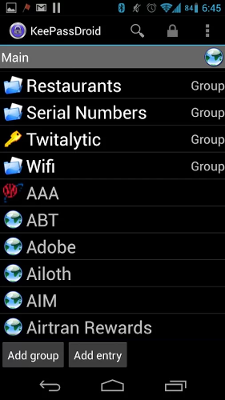 KeePassDroid running on Android.
KeePassDroid running on Android.
SpiderOak is not open-source so it’s not ideal, but unlike Dropbox and Google Drives, it supposed to handle encryption and decryption locally with a locally stored key. Because of that, I trust it slightly more than I trust Dropbox and Google Drive.
Nothing is perfect and this includes this setup as well. Two disadvantages of this setup are:
-
It requires a bit more work to initially set it up and it’s not as integrated as 1Password or LastPass. After you initially set it up though, it requires no additional effort besides pressing global “auto-type” key and entering your master password.
-
If you want to avoid database synchronization conflicts with KeePassX, you should avoid editing database files on multiple devices at the same time.
Database file with your passwords is an encrypted binary file and as such, a general purpose synchronization services can’t figure out what has changed and transparently merge those changes for you.
This is personally not a problem for me because I only edit the database on my laptop and I use other devices (phone, tablet) in read-only mode.
Conclusion
I believe that when dealing with crypto and password managers, using open solutions is very important. As such, KeePassX and their friends offer a superior alternative to other closed-source proprietary solutions.
It’s important to remember though that using an open solution by itself is not enough and doesn’t protect you against targeted attacks. Anyway, that’s a whole different topic and out of scope of this post.
If you want to know more about targeted attacks and how you can protect against them using signed software and deterministic build process, I recommend reading the following blog posts which describe how Tor project recently migrated to a more deterministic build process: